In yet another spate of attacks on prominent digital currency entities and hardware wallets, Trezor has warned its community of users about a potential phishing campaign it is currently investigating.

According to Twitter reports from Trezor users, an email that looks very legit was sent out claiming that the targeted victims have been exposed to a form of a data breach. The email was sent as though it came from Trezor support, and it included a call to action prompting users to download the latest version of the supporting application.
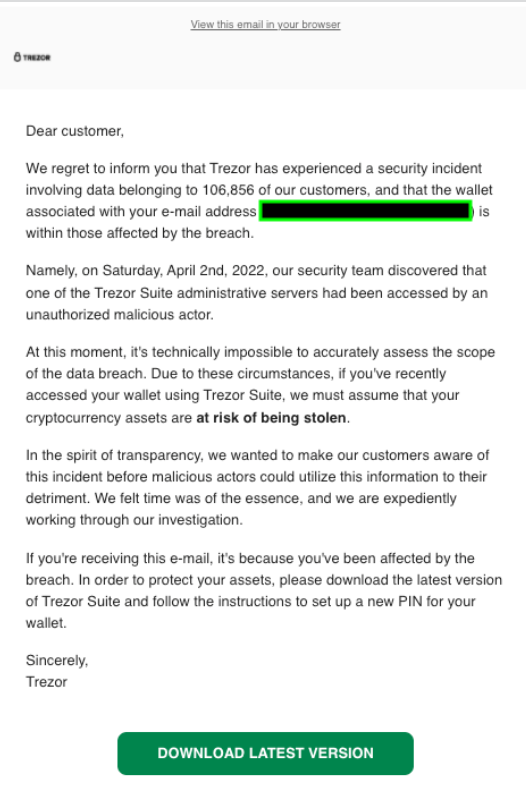
In response to a broad-based user’s complaints, Trezor issued a statement on its official Twitter account saying;
“We are investigating a potential data breach of an opt-in newsletter hosted on MailChimp. A scam email warning of a data breach is circulating. Do not open any email originating from [email protected], it is a phishing domain,”
As the investigations progressed, Trezor informed its community that MailChimp, where the emails originated from, had been compromised recently.
“MailChimp have confirmed that their service has been compromised by an insider targeting crypto companies.”
As the platform works hard to unravel the root cause and the perpetrators of the hack, the entire community is riled up, bemoaning the insecurities that come with the use of cold wallets that Trezor is supposedly one of the biggest in the industry.
Related data breaches have become frequent in the digital currency ecosystem as cybercriminals explore new avenues to rip users off their hard-earned money. In one of the most recent attacks, BlockFi, an American cryptocurrency platform to buy, sell and earn crypto, confirmed last month that some of its client’s data stored on Hubspot, a Customer Relationship Management platform, was compromised.
While the Trezor and BlockFi data breaches did not result in a known loss in cash, they still did not wade off the need to bolster the entire security infrastructure of the global crypto ecosystem, which hackers have continued to exploit.
Image source: Shutterstock