A phishing attack last week gave attackers access to email and files at the California State Controller’s Office (SCO), an agency responsible for handling more than $100 billion in public funds each year. The phishers had access for more than 24 hours, and sources tell KrebsOnSecurity the intruders used that time to steal Social Security numbers and sensitive files on thousands of state workers, and to send targeted phishing messages to at least 9,000 other workers and their contacts.
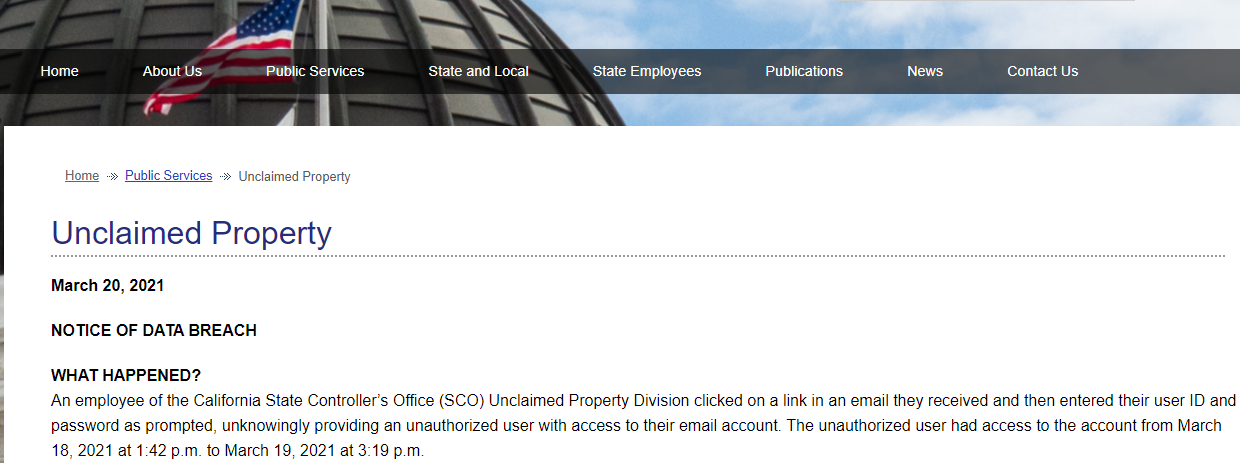
A notice of breach posted by the California State Controller’s Office.
In a “Notice of Data Breach” message posted on Saturday, Mar. 20, the Controller’s Office said that for more than 24 hours starting on the afternoon of March 18 attackers had access to the email records of an employee in its Unclaimed Property Division after the employee clicked a phishing link and then entered their email ID and password.
“The SCO has reason to believe the compromised email account had personal identifying information contained in Unclaimed Property Holder Reports,” the agency said, urging state employees contacted by the agency to place fraud alerts on their credit files with the major consumer bureaus. “The unauthorized user also sent potentially malicious emails to some of the SCO employee’s contacts.”
The SCO responded in an email that no state employee data was compromised.
“A single employee email account was briefly compromised by a spear phishing attack and promptly disabled,” SCO spokesperson Jennifer Hanson said. “SCO has notified the employee’s contacts who may have received a potentially malicious email from the unauthorized user. SCO team members have identified all personal information included in the compromised email account and begun the process of notifying affected parties. The Controller is going over and beyond the notification requirements in law by providing both actual mailed notification and substitute notification in an effort to ensure the broadest possible notification.”
A source in an adjacent California state agency who’s been tracking the incident internally with other employees says the SCO forgot to mention the intruders also had access to the phished employee’s Microsoft Office 365 files — and potentially any files shared with that account across the state network.
“This isn’t even the full extent of the breach,” said the California state employee, who spoke on condition of anonymity.
The source claims the intruders stole several documents with personal and financial data on thousands of state employees, and then used the phished employee’s inbox to send targeted phishing emails to at least 9,000 California state workers and their contacts. In a follow-up response to those claims, the SCO said its “IT security staff were able to determine — based on the same logs that identified the intrusion — that no access was made to any Office 365 files other than the employee’s mailbox.”
The State Controller is the Chief Fiscal Officer of California, the sixth largest economy in the world. Source: sco.ca.gov.
Many attackers can do a great deal of damage with 24 hours of access to a user’s account. And spear-phishing others that frequently interact with the SCO via email could land the bad guys even more access to state systems. The SCO holds an enormous amount of personal and financial information on millions of people and companies that do business with or in the state.
Organizations hoping to improve internal security often turn to companies that help employees learn how to detect and dodge email phishing attacks — by sending them simulated phishing emails and then grading employees on their responses. The employee said that until very recently California was using one such company to help them conduct regular employee training on phishing.
Then in October 2020, the California Department of Technology (CDT) issued a new set of guidelines that effectively require all executives, managers and supervisors to know all of the details of a phishing exercise before it occurs. Which suggests plenty of people who definitely should get phish tested along with everyone else won’t get the same ongoing training.
“Meaning, such people will not be tested ever again,” the state agency source said. “It’s utterly absurd and no one at CDT is taking ownership of this kludge. The standard was also written in such a way to effectively ban dynamic testing like you see in KnowBe4, where even an administrator won’t know what phishing template they might receive.” [Full disclosure: KnowBe4 is an advertiser on this site].
The CDT issued the following statement in response: “SCO informed CDT they have contained the phishing attack. The characterization of the CDT phishing exercise standard is incorrect. Before phishing tests in any state agency are performed, internal business units are advised to coordinate to avoid disruption or operational impact to public services. Supervisors and managers are routinely tested without advance notice to ensure employees at every level are aware of security hazards and can learn how to avoid them.”
Update, 3:44 p.m. ET: Added comment and response from the California SCO.
Update, 5:38 p.m. ET: Added additional comment from SCO about cloud access.
Update, 6:58 p.m. ET: Added response from CDT.