Ransomware needs to be on your radar. Here’s why.
Ransomware Review
Ransomware is a cyberattack where cybercriminals take over an organization’s computer network with malware. Once they assume control, the criminals demand a ransom to restore the victim’s encrypted data access. With an estimated generation of $412 million in 2020 alone1, the frequency of these attacks is growing.
At Experian, we handle many data breach cases and know that 7 of 10 breaches involve ransomware. This summer, NetDiligence dedicated a panel at its Cyber Risk Summit on the Lifecycle of a Ransomware Event and invited us to talk about our solutions to help business leaders prepare to minimize interruptions spurred by ransomware.
The lifecycle of a ransomware attack includes five stages:
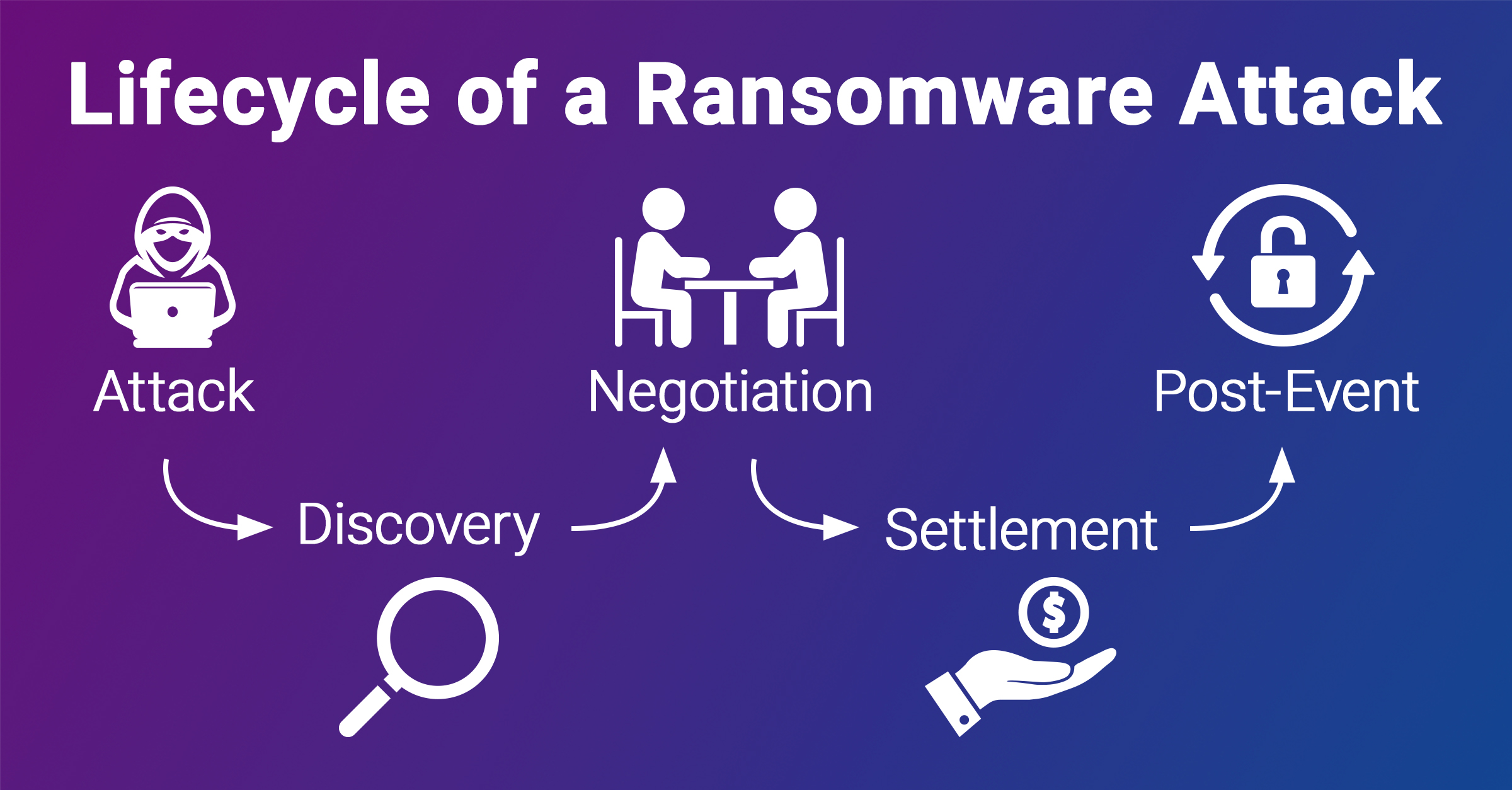
1. Attack
Bad actors attack to discover assets, take data, extort it for direct payment, or profit from reselling data on the dark web. They can also launch a ‘double-take’ attack: first collecting ransom to access data and demanding secondary payment to keep it off the dark web. Hackers prey on company networks, searching for vulnerabilities and accessing encrypted files through phishing or planting malicious links to infect the network with malware. More than double the global rate of 14%2, U.S ransomware attacks have become more aggressive, accounting for 30% of all cyberattacks in 20202. At Experian, we’ve seen an even higher occurrence, with 59% of the events serviced 2021 to date involving ransomware.
2. Discovery
Once attackers infiltrate a system, they demand a ransom for the decryption key to unlock the encrypted files. Companies usually discover the attack through a ransom note emailed to an executive, a file left on a server, or even a flashing warning on all connected computers. If they leave a message including their contact information, ransom sum, payment delivery time, and consequences for unmet conditions, such as tipping off the media, releasing stolen data, or selling it on the dark web.
Next, companies will contact their cyber insurance carrier to log stolen information, get systems back online, navigate legal issues, and facilitate hacker negotiations. Since only about one-third of companies have cyber insurance, most will rush to hire cybersecurity counsel post-attack3, amounting to more stress and delays since it can take months for large companies or those without backups to determine the extent of the damage.
At Experian, almost all events involving ransomware take about 20% more time to begin breach notification. Whether there is an incident plan in place or not, companies experience immense panic.
3. Negotiation
Typically, a company will hire a professional, either directly or through their cyber insurance, to negotiate with hackers. While hackers expect price haggling, the ransom price could still be hefty. According to the cybersecurity firm, Coveware, the average ransom was $154,000 in Q4 2020, down from $230,000 the year before4. But hackers can drive up the price. Prime example: JBS, the world’s largest meat processor, paid an $11 million ransom in June 2021 to prevent customer data from being compromised.
In a perfect world, the ransomware negotiation process goes this way:
- Establish communication with the attackers
- Obtain proof of decryption
- Obtain data exfiltration proof
- Negotiate a (huge) discount
- Celebrate
Unfortunately, negotiations can be tricky, and the process rarely goes this way. Sometimes attackers go “dark” or request additional payments. Additionally, decryption tools may have bugs that skip mapped network drives or skip folders with long paths and unusual characters.
An investigation is key to determine how hackers got in, what was exposed, and if they still have access—knowing exactly how and what was compromised will help in the negotiation.
4. Settlement
After the ransom negotiations are over, companies must carefully consider the strategy behind the decision to pay or not to pay the ransom. The FBI generally discourages ransom payments because they may entice other criminals to engage in ransomware and paying does not guarantee data recovery. Additionally, the Office of Foreign Asset Control (OFAC) has payment bans and restrictions that support national security that must be upheld or face fines. At this stage, companies need to ensure that the ransom settlement does not violate constantly evolving regulations.
If companies settle, the payment will typically be delivered via cryptocurrency like Bitcoin since it is harder to detect the payees. The hackers will mix the bitcoin for others diluting the currency flow and making it difficult to trace.
5. Post-Event
For many companies, the settlement is just the beginning of ransomware attack costs. Companies will also have to pay to restore back-ups, rebuild systems and implement stronger cybersecurity controls to avoid future attacks. As discussed at the Cyber Risk Summit, here are five recommendations for companies to enforce tighter cyber control:
- Advanced Endpoint Monitoring System
- Restrict Remote Desktop Protocol (RDP)
- Regularly Update Software and Operating Systems
- Implement Password Management Policies
- Establish and Update Incident Response Plan and Ransomware Playbook
Ransomware is just getting started. To minimize the impact of an attack, companies create a proactive preparedness plan. Determining to protect and scan for threats, establish negotiation and payment rules, and external breach communications, is critical.
Breaches are our business at Experian. We know ransomware breaches have more complex FAQs, letter versions, and increased call center escalations.
To learn how Experian’s Reserved Response solution can prepare your business for a data breach, click here.
Sources:
1 Washington Post, “How Ransomware Attacks Work”, July 2021
2 Verizon 2021 Data Breach Investigations Report
3 Washington Post, “Ransomware Axa Insurance Attacks”, June 2021
4 Covewave, “Ransomware Marketplace Report”, Q4 2020